It’s not new that DNS or domain name system is the heart of the Internet because this allow us today to experience a faster browsing experience without anyone having to think about how a search works this is because we trust DNS Privacy. It is because of this trust that we don’t think what could go wrong if our searches were manipulated. The DNS queries such as trying to reach our Bank website through our Corporate Laptop or mobile devices. Looking at the DNS queries, someone can easily build your Digital Profile and use it for their own benefit.
DNS was not built having security in mind, but what if we could use Transport Layer Security (TLS) to provide privacy for DNS. Encryption provided by TLS would defeat eavesdropping and on-path tampering with DNS queries in the network.
What are the DNS Privacy issues?
The most common DNS privacy issues are:
- Passive attacks that eavesdrop on cleartext DNS transactions in-flight.
- What is your DNS Resolver doing with the data?
- Active attacks that redirect clients to rogue servers to monitor DNS traffic.
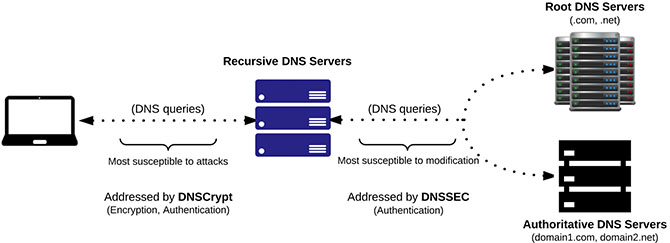
What is the diference between ‘DNSCrypt’ and ‘DNSSEC’?
- DNSCrypt authenticates and encrypts the DNS queries between the endpoint and recursive DNS server. Both endpoint and the recursive DNS server must support DNSCrypt.
- DNSSEC provides authentication between the recursive DNS servers and root DNS servers. The recursive DNS servers and Authoritative DNS Servers must both support DNSSEC.
What DNS Privacy implementations are available?
DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) are the leading solutions for DNS Privacy because they are the only protocols currently standardised by the IETF.
- DNS-over-TLS (DoT): There are implementations (including Stubby a local DNS Privacy stub resolver) and a number of experimental and public servers deployed. This is available through TCP port 853 (standard port).
- DNS-over-HTTPS (DoH): Some implementations (e.g. Firefox) , with DoH it is possible to combine DNS and HTTP traffic on the same port (tcp/443) and make blocking of encrypted DNS much more harder.
- DNS-over-HTTPS (proxied): There are implementations available of proxies that tunnel DNS-over-HTTPS. Google offers a proprietary DNS-over-HTTPS service using a JSON format for DNS queries.
- DNSCrypt: It’s a method of authenticating communications between a DNS client and a DNS resolver. This is an Open Source implementation, not an official standard RFC. Cisco Umbrella implemented this protocol.
What is EDNS Client-Subnet?
EDNS Client-Subnet is a process that includes components of end-user IP address data in requests that are sent to authoritative DNS servers. This can be classified as a grey area of personally identifiable information, but could improve the user experience when a CDN needs to route back traffic through the best path. Cisco Umbrella and Google DNS supports this method.
Conclusion
Several ways of securing DNS are being discussed, some of them already used. DNS-over-TLS seems to be the protocol most adopted so far but DNS as we know it poses a serious risk to all users and systems including IoT.